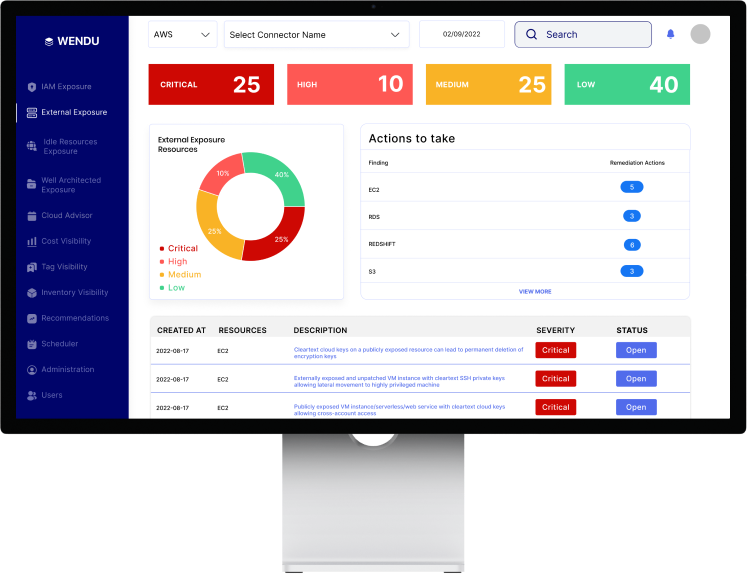
Well Architected Exposure
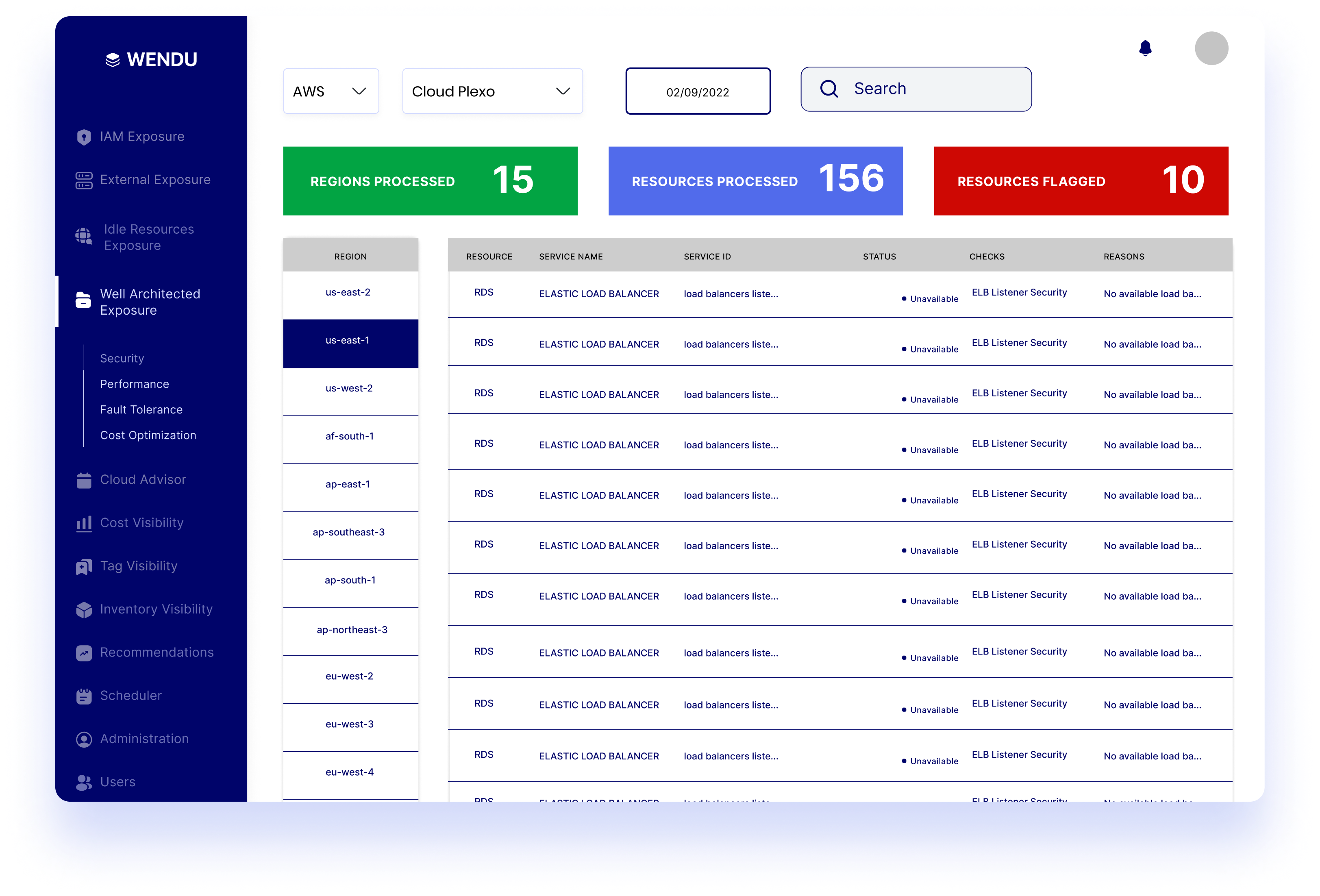
Assess, monitor, and optimize your workload based on the Pillars of the Well-Architected Framework: operational excellence, security, reliability, performance efficiency, and cost efficiency.
Key Features
Gain continuous insights into your cloud workloads and infrastructure

Receive reports on the health of infrastructure based on cloud best practices
Engineer well-architected cloud environments using Wendu
What We Offer
Wendu continuously monitors for misconfigurations of your identity and access management (IAM) across your public cloud to adhere to IAM compliance security best practices and to improve the security posture of your cloud. Threat actors are always looking for ways to exploit vulnerabilities as a result of poor identity and access management practices such as overly permissive identities, weak passwords, unrotated credentials, disabled MFA, accidental public exposures and more.