IAM Exposure
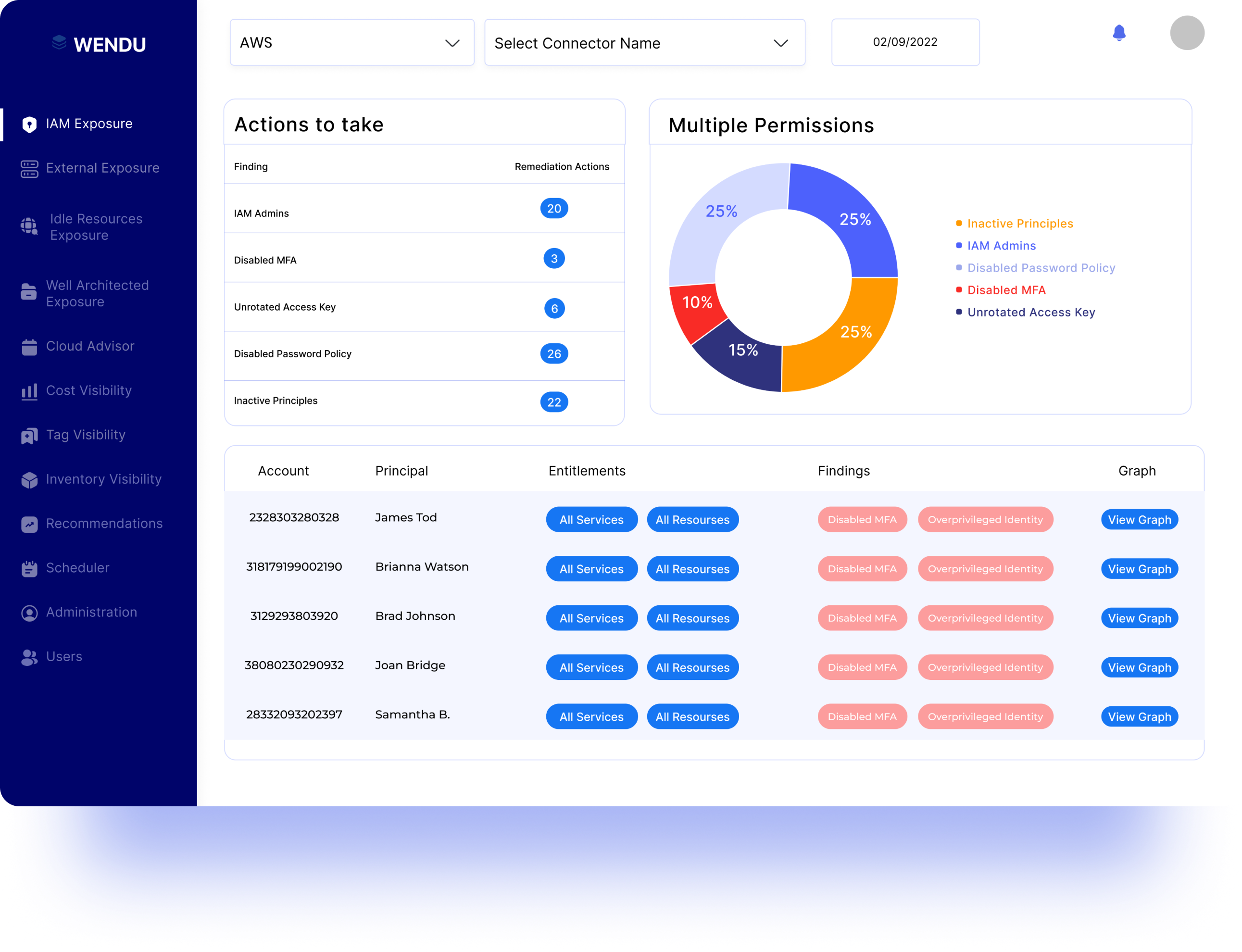
Wendu continuously monitors for misconfigurations of your identity and access management (IAM) across your public cloud to adhere to IAM compliance security best practices and to improve the security posture of your cloud.
Key Features
1
Discover poor identity and access management practices such as overly permissive identities, weak passwords, unrotated credentials, disabled MFA, accidental public exposures and more.
2
Discover misconfigurations of your identity and access management (IAM) across your public cloud to adhere to IAM compliance security best practices and to improve the security posture of your cloud.
3
Improve the quality of identity and access management practices of your cloud estate to reduce vulnerabilities by human factor.
Our Approach
Wendu continuously monitors for misconfigurations of your identity and access management (IAM) across your public cloud to adhere to IAM compliance security best practices and to improve the security posture of your cloud. Threat actors are always looking for ways to exploit vulnerabilities as a result of poor identity and access management practices such as overly permissive identities, weak passwords, unrotated credentials, disabled MFA, accidental public exposures and more.

Learn about the The Greatest Security Vulnerability & more from our case studies.
Learn More