
Cloud Security Strategy - Uber’s Recent Exhaustion Attack Case Study
Cloud Security is becoming increasingly important as more organisations migrate to the cloud. As more organisations adopt cloud computing, security concerns have continued to grow. This has led to an increasing trend in cloud security solutions adoption, such as cloud access security brokers (CASB), cloud security posture management (CSPM), data loss prevention (DLP) solutions, and encryption technologies. These solutions help organisations beef up their cloud security strategies and enforce security policies and compliance
In this blog post, we will talk about cloud security strategies, using Uber’s most recent system breach as a case study, and what organizations must do, in terms of their cloud security strategy to avoid such attacks in the future.
Cloud Security
According to Gartner, Cloud security is the processes, mechanisms and services used to control the security, compliance and other usage risks of cloud computing. It also has to do with the different policies and technologies set in place to protect digital data stored in cloud estates.
Cloud Security helps to protect data, data storage, data servers and runtime environments from malicious attacks, unauthorised access, data breaches, and other security threats. Cloud security also ensures regulatory compliance and helps to protect the privacy of customer data.

Cloud Security Strategy
As more organisations migrate to the cloud and embrace the benefits of cloud computing, ensuring that their data is secure is essential. A good cloud security strategy can help to keep data safe, while also providing organisations with greater control over their data, allowing them to protect their confidential information and intellectual property.
It is highly important for companies to adopt a cloud security strategy because it helps ensure a good security conscious culture within the organisation.
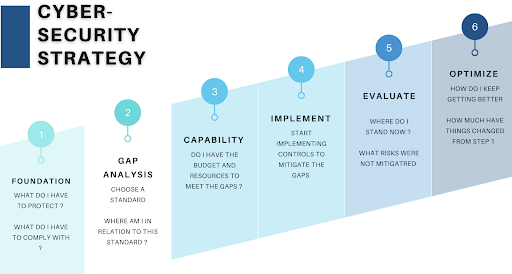
Developing a cloud security strategy can be in theses 6 steps
- Foundation
Here you ask questions such as: What do I have to protect? What do I have to comply with? - Gap Analysis
Choose a security standard, and ask yourself, Where am I in relation to this standard? - Capability
Do I have the budget and resources to comply with this standard? - Implement
Start implementing controls to meet gap - Evaluate
Where do I stand now? What risks were not mitigated? - Optimise
How do I keep getting better? How much have things changed from Step 1?
Uber’s Hacker’s Exhaustion Attack - Case Study
The recent breach on Uber’s system speaks volume and reminds us why we should have an agile and adaptive cloud security strategy. Although, Uber confirmed through a statement on Uber’s website that the company was dealing with a cyberattack. Uber went on to assure the public that it had "not seen" that customers' personal data or trip history had been compromised.
Uber also confirmed that the hacker gained access to their systems through a contractor. Stating that the contractor had their device compromised by malware, giving hackers access to the contractor's username and password, which Uber believes the hacker must have purchased on the dark web.
Uber, however, uses two-factor authentication or MFA to be more IAM compliant and follow security best practices—which shows a good security strategy in place. MFAs or 2FAs, in its most common form, requires users to supply a code sent to them by text, but in other cases, users are simply required to respond to a push notification on their smartphones. You can read more about MFAs as a cloud security best practice here. The security reason being that if someone is attempting to log in, and can prove that they physically have possession of the smartphone associated with that account, then they must be the account owner.
Hackers have found some ways to beat this system by tricking users into helping them, a technique called "remote social engineering." Having access to the user credentials, they attempt to log in over and over, sending a flood of push requests or texts to users asking them to confirm a sign-in.
And in Uber’s case, the hacker apparently used this remote social engineering technique, attempting to log in over and over for more than an hour, thus sending an hour-long bombardment of push notifications to the contractor's phone – enough to make anyone eager to bring an end to it.
Afterwhich the hacker then followed up with a message in which they claimed to be a member of Uber's IT team and asked the contractor to confirm the sign-in on their phone. The contractor complied, possibly with some relief, thus giving the hacker accessThis type of attack is sometimes called an "exhaustion attack".
Security expert Cedric Owen told Wired, “These types of breaches no longer surprise me.”, stating the increasing frequency of such attacks.
Uber, using our 6 step cloud strategy steps, had probably not done the right evaluation of industry threat standards, and fully optimised their cloud security strategy.
You can learn more about Cloud security best practices here.
Wendu and Your Cloud Security Strategy
With the agility and increase in security breach techniques by threat actors and hackers, developing a cloud security strategy must begin with a genuine security culture among staff, and even contractors. Making sure that security strategies are constantly updated, and both staff and contractors are informed of new security threats to your systems.
Cloud security posture management SaaS tools like Wendu help with developing a cloud security culture within your organisation by encouraging a continuous monitoring of the vulnerability of your IT workloads and resources, and also helping you ensure that your staff and contractors are always security compliant. With such tools engraved within your cloud security strategy, your security team will ensure to be up to date (evaluating) with new and latest security cyber threats to your systems, and in turn update your security strategies and policies (optimising).
Learn more about Wendu here, and you can also request a demo to see Wendu in action.