Cloud Security Best Practices: Least Privilege Principle
Hi there! We’re on to the last post on the IAM security best practices. Just a quick recap on this Cloud Security Best Practices series: we began with the foundation of cloud security, which is the Shared Responsibility Model; then we began the IAM best practices with Multi Factor Authentication —what it is and its importance in enforcing IAM access control to your AWS environment; after which we discussed Access Keys, and Password Policiesin our previous post; and today, our focus will be on Least Privilege Principle.
Least Privilege Principle
The AWS Least Privilege Principle is, in simple terms, a principle that encourages IAM policies and roles management to be created, ensuring that every user (human and workload) that has access to your AWS environment, has access only to the resources they need.
For example, in football, you have your goalkeeper, your defenders, your midfielders, and your strikers –together, they make up your football team. However, the outfield players (which is everyone except the goalkeeper) do not have access to the same training resources as the goalkeeper has. Why, you may ask? Exactly, because they do not need goalkeeping training or resources.
Let’s use the F1 team for another illustration, you have the drivers, the mechanics, the electricians, and the supervisors. The drivers do not need to know work on the engine of the vehicle, and hence, should not be given access to work on the engine of the vehicle, same with the electricians. Now, with AWS, see the Supervisor as the Administrator, having seen the capacity, and skillset of his team (users granted access into your environment), the supervisor then grants access to resources that each team (user group), or individual (human or workload user) needs specifically to fulfil their job role, without granting any over privileged access to the other, as in the examples given above.
IAM Security Best Practices and Least Privilege Principle
The Least Privilege Principle is important in ensuring that no user at any time has any over privileged access to any resources they don’t primarily need. This ensures that your resources are only available to those that have the skillset, and expertise to use them –improving the accountability of your resource usage, and maintaining a high quality AWS environment.
You can begin working towards least privileged principles by:
- Creating IAM policies: An IAM policy is an entity that defines users permissions when attached to an identity or resource. IAM policies help you in granting only the permissions required to perform specific job tasks to specific users or workloads. You can learn more about creating IAM policies here.
- Generate IAM policies based on access activity: In creating IAM policies, IAM Access Analyzer helps you generate policies by simply reviewing your AWS CloudTrail logs, and recommended policies based on the user - resource insights gotten from your AWS CloudTrail logs. This can help you start with your IAM policy journey as an administrator. You can learn more about IAM Analyzer here.
- Managing your IAM identity permissions: You might ask why you need to manage your permissions set. Well, for starters, you might have generated your first set of policies using IAM Analyzer, and as your project and team grows or downsizes, or your team gets upskilled, you may need to regularly check which users may have been granted permissions beyond what they require, or even not granted permissions that they may require. In this case, managing (adding and removing) permissions is key to achieving the least privilege principle.
- Refining permissions: By refining, you need to regularly review and remove unused users, roles, permissions, policies, and credentials. In cases where your team has been downsized, it may seem like a no-brainer but believe me, it is a frequent occurrence, where users, roles, permissions, policies, or credentials that are no longer needed still have access to your AWS account. You can always see last accessed information on you IAM page to help you identify inactive principles in your AWS account, and this helps you reduce the number of users, roles, permissions, policies, and credentials that you have to monitor and manage.
Wendu and Least Privilege Principle
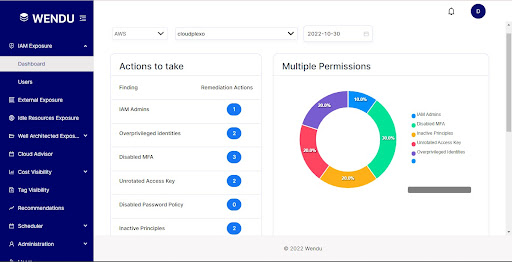
With Wendu, you don’t need to use more than one AWS service to identify any over privileged identities and inactive principles within your AWS account. In one interface, you can ensure that you are achieving the least privilege principle on your AWS account.
Tools like Wendu help you manage your IAM policies set to achieve least privilege principle in your AWS account. Wendu identifies ‘Over Privileged Identities’ and ‘Inactive Principles’ within your AWS account. You can also trace which identities are flagged as over privileged, and which users have become inactive principles based on the last accessed date on Wendu.
Wendu is a 100% API-driven agentless cloud security and management solution. Learn more about Wendu here, and you can also request a here, and you can also request a demo to see Wendu in action.