Cloud Security Best Practices: Access Keys and Password Policies
Great to have you here with us again! For the past two posts, we’ve been discussing Cloud Security Best Practices, with a focus on AWS. We’ve discussed the Shared Responsibility Model, and Multi Factor Authentication; and today we’ll be discussing two other areas that primarily have to do with security best practices within the Identity & Access Management (IAM) of your cloud environment.
We’ll begin with the seemingly easier concept to grasp, Password Policies.
What are Password Policies?
A password policy defines the minimum password strength rule that determines if a new password is valid.
Organizations and Root IAM users can be pretty flexible about customizing their password policies to suit their different organizational internal security and compliance policies. Generally, however, password policies are set around these set of rules:
- Password Length and Formation:
- Minimum and Maximum password length
- Case Sensitivity: the inclusion of lower and uppercase letters
- Inclusion of one or more numerical digits
- Inclusion of special Character inclusions, such as @, #, $
- Prohibition of:
- Words found in password blocklist
- Words that include company name
- Words that include User’s personal information, etc
- Password life cycle:
- Maximum number of days a user can use password until it expires, and has to create new password
Here are AWS Password policy best practices:
- Require password expiration of 90 days
- Require password with:
- Minimum password length of 90 days
- At least one uppercase letter
- At least one lowercase letter
- At least one symbol
- At least one number
Now, onto Access Keys and their cloud security best practices.
What are Access Keys?
Access keys are long-term credentials for an IAM user or the AWS account root user. Access keys are usually required when there’s a need to allow a program, script, or developer to have programmatic access to the resources on your AWS account. Access keys can be used to grant programmatic access to your AWS resources.
Access keys consist of two parts: an access key ID and a secret access key.
Access Keys Cloud Security Best Practices:
- Where possible, use temporary credentials, such as IAM Roles instead of access keys. Learn more about IAM Roles here.
- Rotate your access keys every periodically (preferably, every 90 days)
- Don't embed access keys directly into code
- Use different access keys for different applications
- Remove any unused access keys, and
- Configure MFA on AWS root user and all IAM users
You can learn more about AWS access key management here.
Wendu, Password Policies, and Access Keys
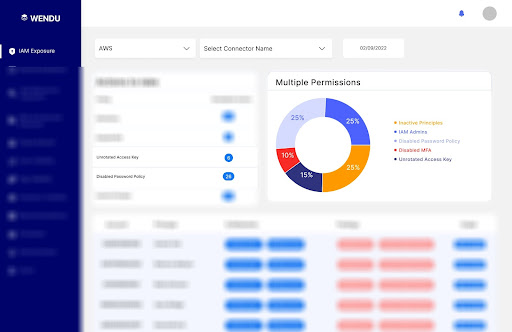
Cloud security platforms such as Wendu enables teams and management to take control and be more accountable of security policies such as rotated access keys, and password policies.
With Wendu, you can identify unrotated access keys, based on your access key policy set, and you can also identify how many IAM users you haven’t enabled your password policy for, as seen in the images below.
Wendu is a 100% API-driven agentless cloud security and management solution. Learn more about Wendu here, and you can also request a demo to see Wendu in action.