Cloud Idle Resources: A Security Risk
Introduction
Cloud idle resources pose a security risk to your organization. Cloud instances continue to register as active with their associated account, even when they are not being used by anyone. This can lead to unwanted service charges, potential network attacks and the possibility of sensitive data leak. To avoid these risks, it's important to find and terminate idle cloud instances periodically.
Why is zombie Resources a problem and why it matters?
Security Vulnerabilities
Zombie servers are unlikely to have the latest software and security patches, which makes them an open door to many enterprise cloud workloads attacks. Zombies are not used, so they are mostly unmanaged and unmonitored. Zombies are an invitation to intruders, detecting security vulnerabilities and stopping attackers is a top business priority.
High Costs
Inefficiencies of idle resources have both large cost impacts. Depending on the size of the organization, these costs can range from hundreds of thousands of dollars to millions of dollars per year, money that can be used more productively.
Environmental impacts
Environmental footprint of idle resources has an impact on the ever-increasing carbon emissions. Global warming as a result of climate change is the single biggest threat to the health and well-being of our society today.
Risky and hard to track the Resource life-cycle
It’s very easy to create a cloud resource such as VMs or a database, but hard to track ownership and purpose over its lifecycle. Example, a cloud resource is provisioned and loses its owner, perhaps because the owner leaves the organization, it’s rare that a new owner is assigned. When a project’s purpose comes to an end, most owners move on to new projects without decommissioning the resource. In Addition, an asset can look active without doing any useful work. Who wants to test it by deleting the VM or data? Few get promoted for such moves.
Achieve Sustainability Goals by Terminating Zombie Cloud Resources
Eliminating zombie cloud resources in your organisation can result in the reduction of carbon emissions contributing to global warming. A proactive effort of discovering and eliminating zombied resources can be a valuable contribution to an organizations sustainability goals. As the world experiences accelerating climate change impacts such as unprecedented heat waves and flooding, the messages of IT efficiency and optimization are resonating
How Wendu Cloud Security Platform can help manage Idle/Zombie resources
Idle or zombie resources are a common issue in cloud computing. They can pose as a security risk and waste of money. The Wendu Cloud Security and management Platform can discover such resources so that you can take action before it becomes a problem.
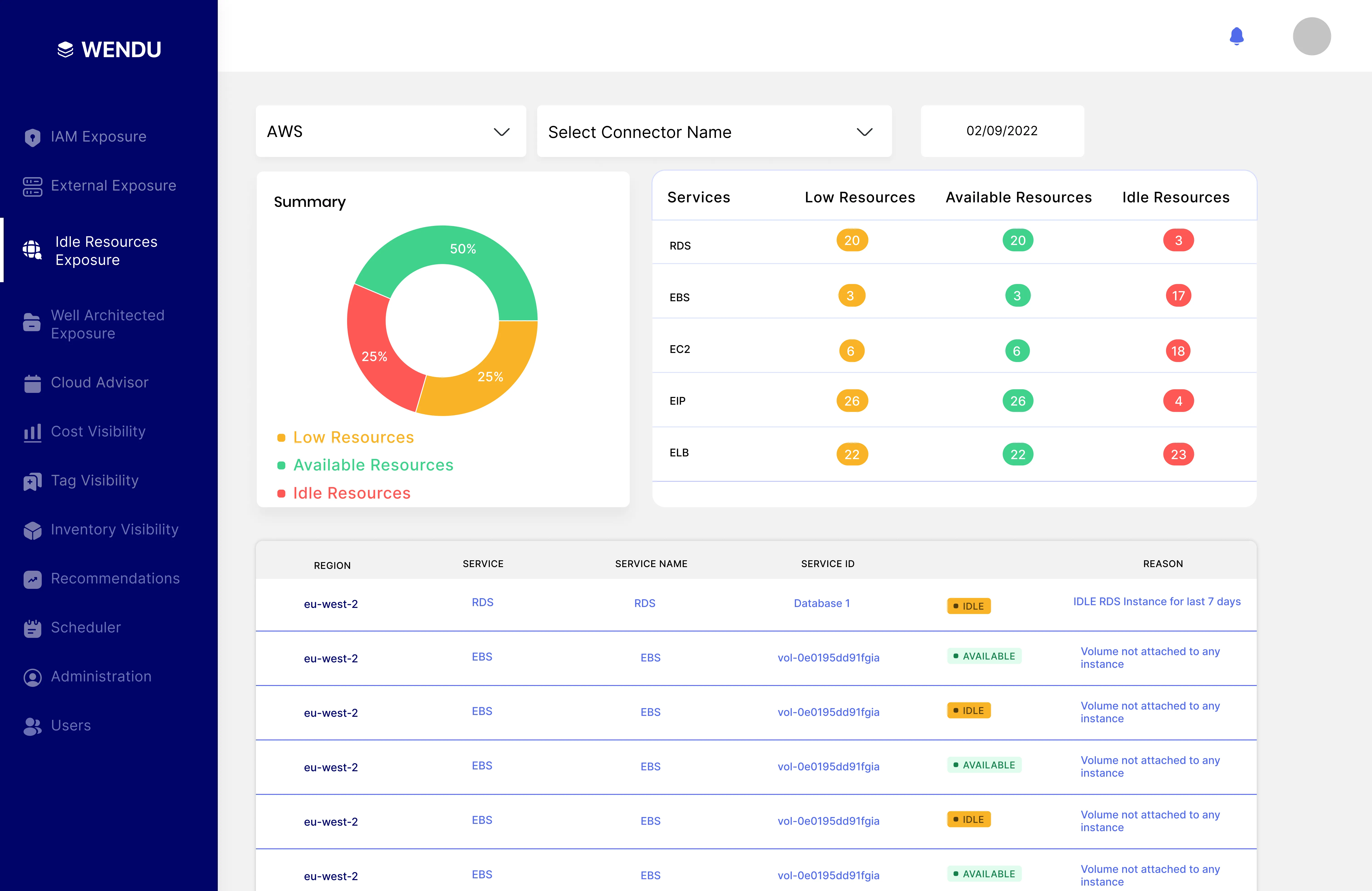
The Wendu Cloud Security and management Platform helps quickly identify such reosurces and enable you to take action to address them. The platform provides an integrated set of tools that enables organizations to manage their security posture, including identifying and remediating zombie resources.
Conclusion
Cloud security is an important component in a cyber security plan. Cloud services can be used for all kinds of applications, including email, web hosting and database storage. The cloud is a great way to store large amounts of data without putting it at risk from cyber criminals or hackers who might want access to your information. However, if you don’t properly manage your cloud resources then it could become one big problem area in your organization as well as pose risks such as exposing sensitive data or become an open door to intruders/attackers.