AWS Well-Architected Framework: Security
Building a secure cloud architecture is a lot like constructing a building. If the foundation is not solid, structural problems can undermine the integrity and function of the building.
When building a cloud architecture on Amazon Web Services (AWS), if you neglect the six pillars of operational excellence, security, reliability, performance efficiency, cost optimization, and sustainability, it can become challenging to build a cloud architecture that delivers on your expectations and requirements.
We’ll begin a series into the five maiden pillars, highlighting how you can use them to build and run your cloud well architected framework. To build a secure cloud architecture on AWS, it must be done using the AWS Security Pillar and in this blog post, we will be touching on the security pillar and how to build a secure cloud architecture.
Before we set the ball rolling, what is cloud architecture?
What Is Cloud Architecture?
Cloud architecture is the systems architecture of the software systems involved in the delivery of cloud computing, which typically involves multiple cloud components communicating with each other over a loose coupling mechanism such as a messaging queue.
Cloud architecture is composed of multiple layers, including the application layer, the platform layer, the data layer, and the infrastructure layer. Each layer provides different services, such as application and platform services, data storage and processing, and networking, to support the needs of the application. Cloud architecture is designed to be flexible and scalable, allowing the system to be adapted to different requirements and workloads.
Just the same way you can’t build a house without architects, a cloud environment cannot be built or deployed without cloud architecture.
AWS Well-Architected Framework
The AWS Well-Architected Framework is a set of best practices that help organizations understand the key areas of cloud architecture and build secure, reliable, and cost-effective applications. The framework provides a set of questions to help evaluate the architecture of an application and identify areas that need improvement.
It also provides guidance on how to best use AWS services to achieve these goals. The framework is divided into six pillars: Operational Excellence, Security, Reliability, Performance Efficiency, Cost Optimization, and Sustainability. Each pillar contains a collection of best practices to help guide application architecture.
If you are building a two storey building, for example, you need pillars to provide firm support. Just as pillars play a vital role in building architecture, the pillars of the AWS Well-Architected Framework help cloud architects build the most secure, high-performing, resilient, and efficient infrastructure possible for their applications.
AWS Security Pillar
The AWS Security Pillar is a set of services, tools and best practices that organizations can use to improve the security of their cloud infrastructure. It includes services such as Amazon Virtual Private Cloud (Amazon VPC) for infrastructure security, Amazon Identity and Access Management (IAM), AWS Shield for DDoS protection, AWS Config for compliance, and AWS Key Management Service (KMS) for encryption.
It also includes best practices such as multi-factor authentication, a secure development lifecycle, and secure application architecture.
The Security pillar enables organisations to protect their data, systems, and assets to take advantage of cloud technologies to improve their security posture.
AWS Security Best Practices
The AWS Shared Responsibility Model: The AWS Shared Responsibility Model is the foundation of all security best practices, and it enables organizations that adopt the cloud to achieve their security and compliance goals. Because AWS physically secures the infrastructure that supports our cloud services, as an AWS customer you can focus on securing your data and workload in the cloud by using the required AWS security services to accomplish that.
Access Control: You’ll want strong security policies to control who can do what. In addition, you want to be able to identify security incidents, protect your systems and services, and maintain the confidentiality and integrity of data through data protection.
Fast Security Incident Response: You should have a well-defined and practised policy for responding to security incidents. These tools and techniques are important because they support objectives such as preventing financial loss or complying with regulatory obligations.
Secure Design Principles
In the cloud, there are a number of principles that can help you secure your cloud security:
- The principle of least privilege: The principle of least privilege enforces separation of duties with the appropriate authorization for each interaction with your AWS resources usingIAM User & Group Roles.
- Enable traceability: Monitor, alert, and audit actions and changes to your environment in real time. Integrate log and metric collection with systems to automatically investigate and take action. This can be done using AWS CloudTrail
- Apply security at all layers: Apply an in depth defence approach with multiple security controls. Apply to all layers (for example, edge of network, VPC, load balancing, every instance and compute service, operating system, application, and code). Services such as AWS NAT Gateways, AWS WAF(Web Application Firewall), AWS Inspector, AWS Shield, etc, help you improve network security, incident response, infrastructure security, as well as other layers within your architecture.
- Automate security best practices: Automated software-based security mechanisms improve your ability to securely scale more rapidly and cost-effectively. Create secure architectures, including the implementation of controls that are defined and managed as code in version-controlled templates using visual workflow services such as AWS Step Functions.
- Data Protection: Classify your data into sensitivity levels and use mechanisms, such as encryption, tokenization, and access control where appropriate. You can ensure you tick the encryption boxes when using AWS services such as S3, or you can add an advanced encryption service such as AWS Encryption SDK.
Wendu & AWS Well Architected Framework - Security
Running a well architected assessment on your cloud architecture using the AWS Well Architected Tool can look anything like this:
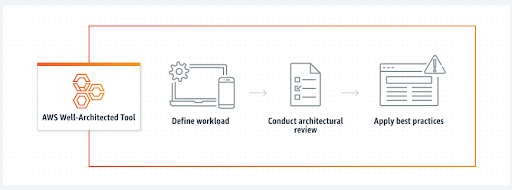
And in reality, it looks like this:

Answering a bunch of questions to determine how secure, reliant, efficient, cost effective, and sustainable your AWS architecture is.
On Wendu, it looks something like this:
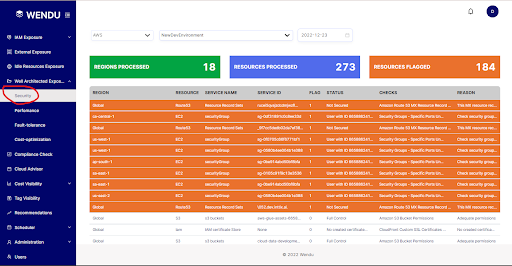
With Wendu, you can run automated well architected assessments to determine how secure your cloud architecture is. This improves your architecture consistently by ensuring you’re following AWS well architected best practices for security!
Wendu also serves as a CSPM for vulnerability management and security compliance, such as GDPR, PCIDSS, HIPAA, and others.
Learn more about Wendu here, and you can also request a demo to see Wendu in action.