Blogs & Case Studies
What is Security Management in the Cloud? - Unlocking the Basics.
In the ever-evolving landscape of cloud technology, security management stands as a crucial pillar to ensure the integrity, availability, and confidentiality of your data and applications.
Read More
Behind the Scenes - How Cloud Security Works to Keep You Safe.
In the dynamic realm of cloud technology, security plays a pivotal role in ensuring your data and applications remain safeguarded from evolving cyber threats.
Read More
Cloud Security vs Cloud Computing - Understanding the Differences.
The realm of cloud technology encompasses two essential pillars: cloud security and cloud computing. While they share a common foundation, they serve distinct purposes...
Read More
Computer Cloud Security System Explained.
In today's data-driven world, the security of your digital assets is paramount. Cloud computing has brought unprecedented convenience, but it also requires robust security measures.
Read More
Exploring Cloud Security Technology - Safeguarding Your Cloud Environment.
In the dynamic landscape of modern business operations, securing your cloud environment is paramount. The advent of cloud security technology has revolutionized how organizations protect their sensitive data and critical assets. In this blog post, we will delve into the role of artificial intelligence and machine learning in cloud security, shed light on prevalent cloud security threats and vulnerabilities, and guide you on integrating cloud security technology into your overarching strategy.
Read More
Exploring Cloud Management Solutions in Nigeria.
In the dynamic landscape of modern business operations, securing your cloud environment is paramount. The advent of cloud security technology has revolutionized how organizations protect their sensitive data and critical assets. In this blog post, we will delve into the role of artificial intelligence and machine learning in cloud security, shed light on prevalent cloud security threats and vulnerabilities, and guide you on integrating cloud security technology into your overarching strategy.
Read More
Cloud Infrastructure Solutions and Driving Nigerian Business Growth
In the dynamic landscape of Nigerian business, leveraging cloud infrastructure solutions has emerged as a game-changer
Read More
Demystifying Cloud Security - Understanding Cloud Security Solutions.
As the cloud landscape continues to evolve, ensuring robust security for your cloud infrastructure is of paramount importance.
Read More
Unlock Cost Optimization Strategies with our Top 10 Cloud Cost Monitoring Best Practices.
In today's digital landscape, cloud computing has become a game-changer for businesses,offering unmatched scalability, flexibility, and cost-efficiency. However, without proper monitoring...
Read More
Maximising Cloud Cost Savings and Security with Wendu Mobile App
In today's digital landscape, businesses are increasingly leveraging the power of the cloud for their operations. That's why we're excited to introduce our cutting-edge mobile app to complement our web app to show you the health of your cloud on the go.
Read More
Shortfalls of Agent based security scanning
Agent based security scanning is a popular way to improve security by adding an extra layer of protection to your environment. However, the fact that agents run locally on systems rather than remotely makes them vulnerable to attack.
Read More
Revolutionising security through SecFinOps
As a security team we have to deal with many different aspects of our jobs. We need to ensure that our environments are secure, and that the data we create is safe. But what if there was more to it?
Read More
Cloud Idle Resources: A Security Risk
Cloud idle resources pose a security risk to your organization. Cloud instances continue to register as active users with their associated account, even when they are not being used by anyone.
Read More
Ensuring Cloud Security - Protecting Your Business in the Digital Age
The Web has made it more straightforward to lead business and offer data across the world, yet alongside these advantages come chances.
Read More
Cloud Security and Shared Responsibility Model
Cloud security, like every other security mechanism or system in life, operates on a shared responsibility model. Your building security operates on a shared responsibility model while you must secure your personal belongings within your office.
Read More
Mitigating Human Error to Preventing Cloud Security Vulnerabilities
The people, process, and technology framework for everything innovation is still very much valid in regards to it being the strength and weakness of innovation. No part of this tri-fold framework is independent of each other...
Read More.5d2773ef.png)
Cloud Security and Multi-Factor Authentication (MFA)
Authentication happens when a user tries to login to a system (network, device or application). The system then requires the user to provide the identity by which the user is known by the system...
Read More
Cloud Security Best Practices: Access Keys and Password Policies
A password policy defines the minimum password strength rule that determines if a new password is valid. This article discusses two other areas that primarily have to do with security best practices within the Identity & Access Management (IAM) of your cloud environment.
Read More
Cloud Security Best Practices: Least Privilege Principle
The AWS Least Privilege Principle is, in simple terms, a principle that encourages IAM policies and roles management to be created, ensuring that every user (human and workload) that has access to your AWS environment, has access only to the resources they need.
Read More
Cloud Wastes And How To Avoid It: Idle Resources
Cloud wastes come from cloud resources that are not being paid for but not being used; and this goes against the very pricing value proposition that cloud computing offers to its users –which is that you pay for only what you use!
Read More
Cloud Wastes And How To Avoid It: Poor Cloud Utilisation
In AWS reInvent 2019, it was reported that among enterprise users, 35% of their annual cloud spend was waste, amounting to over $10 billion. Cloud wastes are money being paid to your CSP for cloud resources and services that are not being used.
Read More
AWS reInvent: Key Takes on Cloud Security, Management, and Adam Spelinsky’s Remarks on Cloud Today
In this post, we’ll be discussing some of these debutant services in the areas of security, identity & compliance, and cloud management. For some of us who are fairly new to AWS, security, identity & compliance services focus on services that enable you to secure your workloads, data, applications, and your AWS account in general.
Read More
What Are Organisations Doing To Optimise Cloud Costs?
As companies are moving their digital assets, services, databases, IT resources, and applications to the cloud, one question remains persistent; how do we manage our cloud cost? How do we make sure we’re leveraging the pay-as-you-go or ‘pay only for what you need’ pricing structure, and not spending more than we should be spending?.
Read More
What policies are organisations implementing to use the cloud more securely?
Cloud computing remains an integral part of business today. The cloud gives you access to more applications, improves data accessibility, helps your team collaborate more effectively, and provides easier content management.
Read More
Cloud Security Solutions Organisations Are Adopting
The rise of companies migrating to the cloud has become popular because it gives organisations the advantage of being able to scale up and down quickly without having to worry about downtime.
Read More
Cloud Spend: CAPEX vs OPEX
The flexibility and scalability inherent in cloud computing has fuelled a dramatic increase in the adoption of cloud services and technologies. Organisations have been moving from on-premise servers to virtual servers, hosted private clouds...
Read More
Cloud Security Strategy - Uber’s Recent Exhaustion Attack Case Study
As more organisations adopt cloud computing, security concerns have continued to grow. This has led to an increasing trend in cloud security solutions adoption...
Read More
Securing Your IT Assets in the Cloud
In the business world, data is everything. From client information to financial records and more, your company’s data is its lifeblood. In today’s digital age, that data is increasingly stored in the cloud.
Read More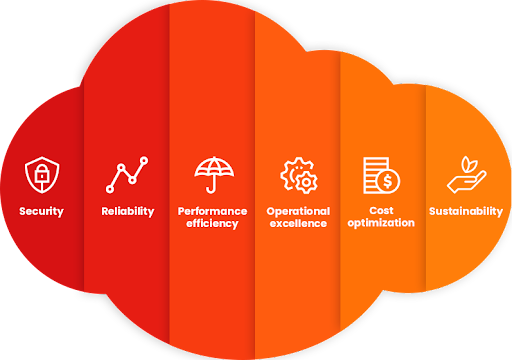
AWS Well-Architected Framework: Security
When building a cloud architecture on Amazon Web Services (AWS), if you neglect the six pillars of operational excellence, security, reliability, performance efficiency, cost optimization, and sustainability, it can become challenging to build a cloud architecture that delivers on your expectations and requirements.
Read More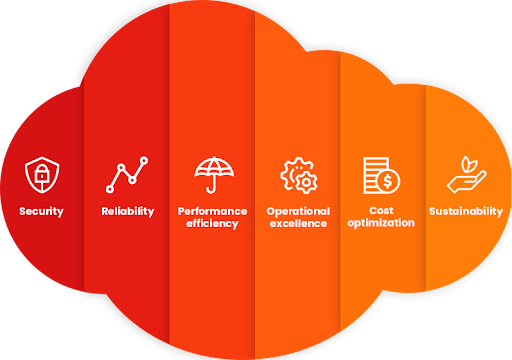
AWS Well-Architected Framework: Cost Optimization
In this blog post, we will be looking at another pillar- cost optimization. In this blog post, we will explore the pillar emphasising how you can build a cost-optimised architecture as we did on the security pillar.
Read More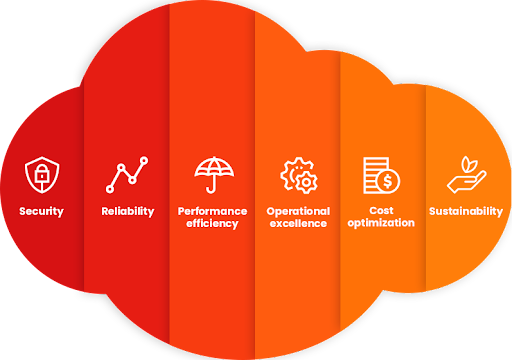
AWS Well-Architected Framework: Reliability
In this blog post, we will be looking at another framework pillar- the reliability pillar which focuses on workloads performing their intended functions and how they recover quickly from failure to meet demands.
Read More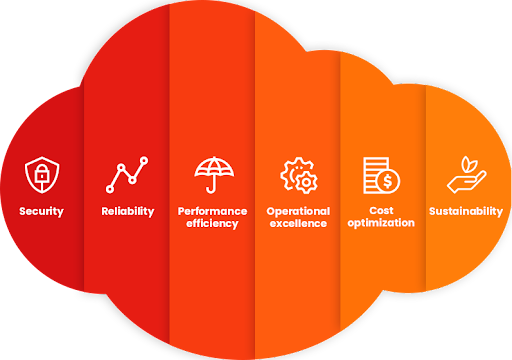
AWS Well-Architected Framework: Performance Efficiency
Building on the foundation we've laid on what cloud architecture is, this blog post will address how to build an efficient cloud architecture, best practices and principles.
Read More
AWS Well-Architected Framework: Operational Excellence
This blog post aims at roofing the building by giving insights into the Operational Excellence Architecture with best practices and tips on how to build an Operational Excellent Cloud Architecture. The Operational Excellence Architecture focuses on running, monitoring systems, and continually improving processes and procedures.
Read More
Setting Up Your AWS Budget and Billing Alerts
In this series of blog post, we’ll discuss setting up budgets on your AWS bills and cost alarms to compliment your budgets..
Read More
Management Vs Tech team: Who's Responsible?
Cloud costs can quickly get out of control, especially when there isn’t a cloud cost management system in place. This usually occurs when individuals spin up instances across different teams.
Read More
Cloud Security Without Breaking The Bank - For SMEs & Startups
Small businesses and startups operate on a very small scale with limited resources. Usually, strengthening their cloud security infrastructure is not as prominent as building a business. A report by CyberPeace Foundation reveals that nearly 47% of SMEs have no clue about managing cyber risks. In addition, about 60% of such small enterprises that turn victims of security breaches go out of business within six months.
Read More
Rightsizing Your AWS Estate - Part 1
Are you tired of overspending on your AWS estate? Are you struggling to optimize your resources and reduce costs? Look no further, because in this blog post, we will be discussing the concept of rightsizing your AWS estate.
Read More
Rightsizing Your AWS Estate - Part 2
In this blog post, we will be focusing specifically on EC2 rightsizing. We will be diving deeper into the different methods and tools available for rightsizing EC2 instances, and providing tips and best practices for maximizing your savings.
Read More